Event-Driven Architectures demystified: from Producer to Consumer – part 2
11 February 2026 - 17 min. read
Eric Villa
Solutions Architect
 In the first article of our 3 part journey on how to break down a Monolithic application we have started talking about the advantages of a distributed application composed of microservices over a monolithic one. In this second part, we will start approaching techniques and tips to help you overcome the migration process in a more secure and aware way
In the first article of our 3 part journey on how to break down a Monolithic application we have started talking about the advantages of a distributed application composed of microservices over a monolithic one. In this second part, we will start approaching techniques and tips to help you overcome the migration process in a more secure and aware way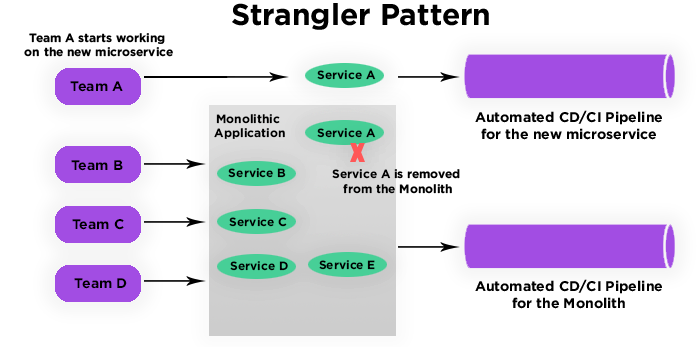 This approach is very good for a number of reasons:
This approach is very good for a number of reasons: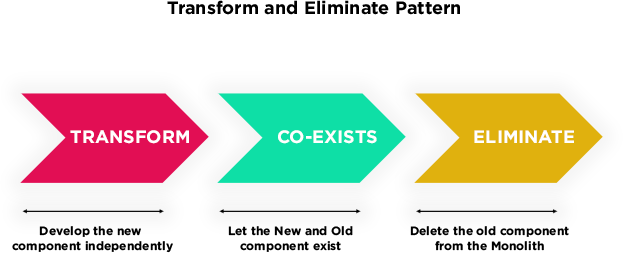 To start extracting elements of your business logic, especially if you are new to this pattern, choose those that have:
To start extracting elements of your business logic, especially if you are new to this pattern, choose those that have: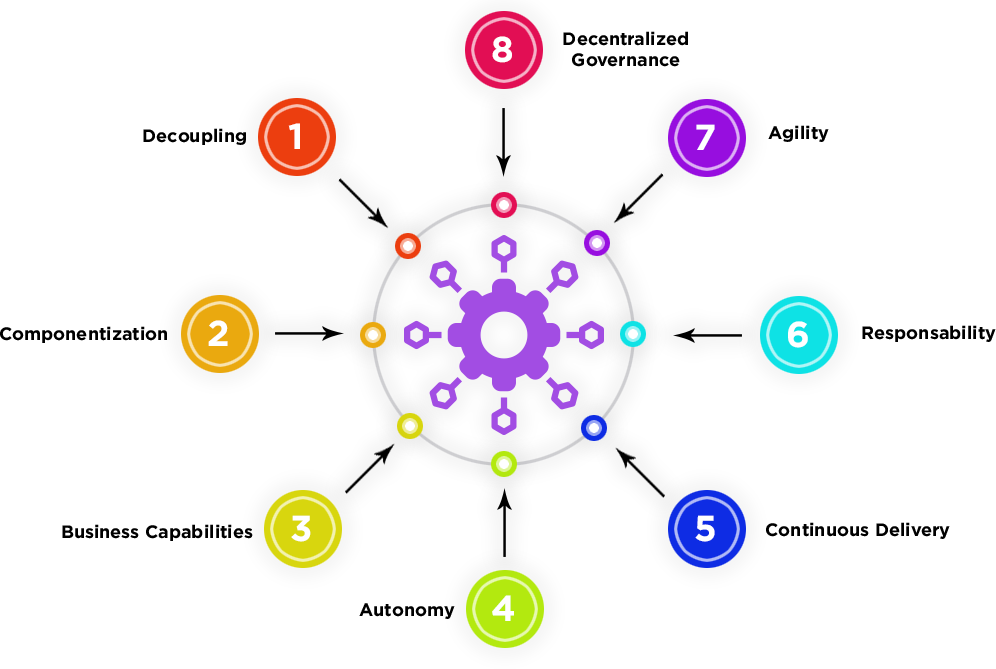 In this second part of our 3-article journey on how to break down a Monolithic application we have started to deep dive in some well-known techniques and ideas that helps dev and business team to decide when and how we can split legacy code in atomic and independent microservices, how we can approach the migration life-cycle and in general what properties a microservice must have to be considered one. In the next article we will conclude our journey describing how to effectively start coding your microservices, how to approach complex code with high intellectual value and also when switching to a microservices-ecosystem may not be a good choice.Stay tuned!
In this second part of our 3-article journey on how to break down a Monolithic application we have started to deep dive in some well-known techniques and ideas that helps dev and business team to decide when and how we can split legacy code in atomic and independent microservices, how we can approach the migration life-cycle and in general what properties a microservice must have to be considered one. In the next article we will conclude our journey describing how to effectively start coding your microservices, how to approach complex code with high intellectual value and also when switching to a microservices-ecosystem may not be a good choice.Stay tuned!